In the digital world, one becomes very prone to different kinds of cyber-attacks. With more black hat hackers around who use security vulnerabilities to their advantage, it has now become very important to protect oneself online. In fact, black hat hackers make use of their skills to steal sensitive data, intrude into networks, and cause widespread harm. With proper precautions in place, one is at a good position of safeguarding personal information and minimizing any probabilities of falling into the trap of such cybercriminals.
The following tutorial will cover 10 tips that will get you started on how to protect yourself against Black Hat hackers and how to keep safe in the increasingly unsafe world of cyberspace.
Table of Contents

1. Understand the Threat: What Are Black Hat Hackers?
What Skills Do Black Hat Hackers Possess?
Before going into protection strategies, it is necessary to understand who black hat hackers are and what skills they possess. Black hat hackers are those who take advantage of their advanced knowledge of computer systems, networks, and programming illegally. It would include the knowledge of coding, encryption of data, social engineering, and how wi-fi works-meaning that they manage to bypass security measures and infiltrate sensitive data.
Is It Legal to Hack Black Hat SEO?
Note that hacking, regardless of its motivation, is illegal except when it falls within the scope of ethical hacking practices. The white hat hackers, for example, use the same skills to legal ends, such as testing the security systems and finding the loopholes in companies where these should be fixed. Black hat hacking is a criminal activity, and those found guilty may face grave legal consequences.
2. Strong and Unique Passwords
Creating strong, unique passwords for different sites remains one of the easiest yet intelligent methods for keeping the black hat hackers at bay. Poor passwords invite hackers, who in most cases attempt to crack such using brute force methods.
Best Practices for Password Security
- Create Complex Passwords: Use a combination of letters, both uppercase and lowercase, numbers, and special characters.
- Avoid common words and phrases for passwords, including anything easily guessed, like your name, birth date, or “password.”
- Use a Password Manager: A password manager can create and store the complex passwords for you, saving you from memorizing each password.
How to Protect Yourself from Black Hat Free
By following this, you will be able to stay safe from black hat hackers without having to spend one single penny. One of the easy ways, yet highly efficient, to keep accounts and personal information safe.
3. Enable Two-Factor Authentication (2FA)
Two-factor authentication helps keep hackers out by adding another layer of difficulty that requires entry not only of a password but also some other form of verification. This is usually done by sending a code to your phone.
How 2FA Works
Once you attempt to sign in-once you’ve typed your password, anyway-you’ll be prompted to enter a code that was dispatched to your mobile device or a randomly generated code from an authenticator app. That even if a black hat hacker got hold of your password, they still couldn’t get into your account without that second form of authentication.
2FA Benefits
2FA drastically reduces the chances of unauthorized access; hence, it’s one of the most effective ways to protect yourself from black hat hackers. Many online services offer the ability to enable 2FA, including social networks, email, and banking websites, so use it when available.
4. Keep Your Software Up-to-Date
Why Software Updates Matter
Software updates are crucial for keeping your devices safe from black hat hackers. This is because software updates often patch security gaps that hackers may otherwise take advantage of. From operating systems to browsers to mobile apps, everything needs to be updated for cyber security.
Automatic Updates: The Easy Route
Activate auto-update in all your devices to be sure you are covered each day. This way, you shall enjoy recent security patches when they become available, thus little time is available to the advantage of any attacker.
5. Be Cautious with Public Wi-Fi Networks
The Dangers of Public Wi-Fi
Public Wi-Fi, like those in cafes, airports, and hotels, are known as insecurities. Black hat hackers more often will intercept data on such networks and steal personal information for attacks.
How to Protect Yourself on Public Wi-Fi
- Avoid Sensitive Data Access: Refrain from logging into banking or any sensitive accounts while using public Wi-Fi.
- Use a VPN: A Virtual Private Network encrypts your Internet connection, which greatly decreases the likelihood of hackers intercepting your data.
- Turn Off Sharing: Disable file sharing and other such features that may expose your device to other users on the network.
In this way, you get to protect yourself against black hat hacking even when mobile.
6. Educate Yourself on Phishing Scams
What Is Phishing?
A phishing technique is adopted by a black hat hacker who tries to dupe people into giving away personal information like passwords or credit card numbers. They mainly send fake emails or messages, which appear to be from legitimate sources.
How to Identify Phishing Attempts
- Verify the sender’s email address. Most of the time, phishing emails are sent by using email addresses with spelling errors or extraneous characters.
- Look for Red Flags: Most phishing emails tend to create urgency with messages like an account would be closed if no action is taken right away.
- Avoid Clicking Links: If an email seems suspicious, instead of clicking the links within it, go directly to the official website by typing the URL into your browser.
Protect yourself from Phishing
Being informed about phishing techniques and being wary of emails or messages can actually save a person from falling victim. Always confirm the sender before surrendering sensitive information.
7. Antivirus and Anti-Malware Software
The Function of Antivirus Software
Antivirus and anti-malware applications are handy weapons in fighting against black hat hackers. They can find and remove malicious software that could compromise your security, including viruses, ransomware, and spyware.
Choosing the Right Software
Look for good, solid antivirus that will give you real-time protection with regular updates and the ability to deeply scan. A few of the best rated include Norton, McAfee, and Bitdefender.
Perform Regular Scans and Updates
Set your antivirus to update and run automatically on a regular basis to detect and remove programs with malicious intent. Of course, this proactive behavior will protect you against black hat hacking attempts.
8. Secure Your Wi-Fi Network
Why Wi-Fi Security Matters
Unprotected or improperly secured home Wi-Fi invites the attention of black hat hackers. If such hackers intercept your Wi-Fi, they might steal personal information and launch attacks on other devices connected to the same network.
Best Practices for Securing Wi-Fi
- Change the Default Router Password: Many routers are pre-set with easy-to-guess passwords, even by amateur hackers. Replace this with a strong, unique password.
- Enable WPA3 Encryption: This is the latest and most secure encryption standard for Wi-Fi networks.
- Hide Your SSID: By turning off the broadcast of your network’s SSID-that is, its function or name-you make it more difficult for hackers to find your network.
Follow these procedures so as to protect your home network from a black hat hacker and ensure that internet usage remains private and secure.
9. Backing Up Your Data on a Regular Basis
The Importance of Backing Up Your Data
Backing up your data regularly ensures that you have copies of important files that might get destroyed by certain types of cyber attacks, such as ransomware, whereby hackers keep you out of your files and then request some ransom in return for access.
How to Back Up Your Data
- Use Cloud Storage: Services like Google Drive, Dropbox, or OneDrive can offer you a safe space in the cloud where you will be able to back up your files constantly.
- External Hard Drives: For extra security, you should back up your data onto an external hard drive that is not to be left connected to your computer.
The Benefits of Regular Backups
Having a backup system means that, even if some black hat hacker wipes out your data, you are protected from losing any critical information. In fact, this can be one of the best ways to defeat any ransomware attack.
10. Educate Yourself and Stay Informed
The Importance of Cybersecurity Awareness
One of the best ways to protect oneself against black hat hackers is probably by keeping updated about the latest on cybersecurity threats and best practices. Cybersecurity is in constant flux, and new threats surface now and then.
How to Stay Updated
- Follow Cybersecurity Blogs and News Sites: Websites like Krebs on Security, Threatpost, and the official sites of your antivirus provider give regular updates on the latest threats.
- Take cybersecurity classes: Online classes will provide valuable insight into the way hackers work and how to protect one’s self from them.
- Join online communities: Forums, like the cybersecurity subreddit on Reddit or online groups about ethical hacking, can keep you in the know and even help you learn from others.
The Role of Continuous Learning
Continuous learning helps you to stay one step ahead of black hat hackers and protect your personal information effectively. Knowledge is one of the strongest guns in this war against cybercrime.
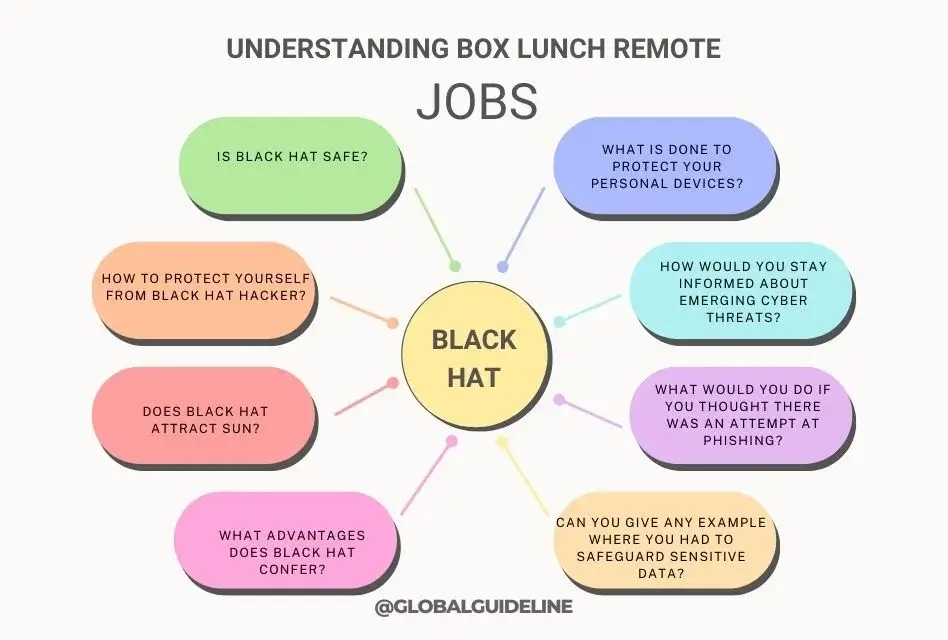
Common Job Interview Questions: Protecting Yourself from Black Hat
How Can I Prove That I Am Informed about Cybersecurity in the Interview?
One good way to impress a potential employer, especially in a job involving IT or cybersecurity, is by demonstrating that you know how to protect against black hat hackers. Here are some common questions:
- What is done to protect your personal devices?
Discuss the strong passwords, 2FA, keeping your software updated, and antivirus programs used. - How would you stay informed about emerging cyber threats?
The following, pertaining to cybersecurity news, would be: taking courses and participating in online communities. - What would you do if you thought there was an attempt at phishing?
Please describe in detail how you would check the sender, not click on suspicious links, and report it to higher-ups. - Can you give any example where you had to safeguard sensitive data?
Give an example from past experience where you took measures to secure the data, highlighting your proactive approach towards cybersecurity.
Tips for Interview Success
- Be Specific: It is more about giving examples and using technical terms when trying to explain something.
- Keep Cool: If you’re asked a technical question during your interview, take a moment to gather your thoughts and come up with a clear, step-by-step answer.
- Show Your Passion: Employers like to believe that you are interested in cybersecurity and take it seriously.
Frequently Asked Questions
Is black hat safe?
No, it is not legal or safe to be involved in or associated with black hat activities. Black hat hackers operate outside the ambit of the law, hence any participation in such activities might attract grave legal implications.
How to Protect Yourself from Black Hat Hacker?
Some of the major ways through which you would have been protecting yourself against black hat hackers are using strong passwords, enabling two-factor authentication, keeping software up to date, exercising care with public Wi-Fi hotspots, and using antivirus. Take full regular backups and keep yourself informed about cybersecurity threats.
Does black hat attract sun?
Speaking of fashion, yes, a black hat can attract more heat since dark colors tend to absorb sunlight better. In any case, this has no relation to cybersecurity or the term “black hat” related to hackers.
What advantages does black hat confer?
There are absolutely no benefits of engaging in black hat activities when it comes to cybersecurity. Black hat activities are considered illegal and unethical. Studying black hat techniques from an ethical perspective, however, helps cybersecurity professionals understand and fight cyber threats more effectively.
Conclusion
Defense against black hat hacking involves becoming very proactive and current about cybersecurity best practices. You will apply the tips to protect your personal information, secure your device, and reduce the chances of being a victim of cyberattackers. Each step you take in relation to using strong passwords, enabling two-factor authentication, or staying updated on emerging threats enhances online security.
The threats keep changing with time, and awareness is considered the best defense against them. Consider making cybersecurity one of your priorities, helping you and your sensitive data stay out of the reach of black hat hackers that are lurking in every corner.